[Update Dec 2022] Save even more with a New 350-401 dumps

First, you’ll need to prepare for the CCNP 350-401 ENCOR exam for $400, which is not a small fee. If you can use the 350-401 dumps to succeed the first time you take the 350-401 ENCOR exam, then why not choose? This can be a huge saving!
Here you can select the newly updated 350-401 dumps https://www.leads4pass.com/350-401.html, to help you successfully pass Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) on your first attempt at an exam.
leads4pass 350-401 dumps have real-world test-room success with a high score of 99.5% to help you pass the Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) exam with ease.
The 866 newly updated 350-401 dumps are verified by a team of experienced experts to ensure you take the Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) exam without fail.
Read some new 350-401 dumps exam questions and answers online for free share
| Number of exam questions | Exam name | From | Release time | Last updated |
| 15 | Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) | leads4pass | Dec 02, 2022 | 350-401 dumps |
New Question 1:
Which Python code snippet must be added to the script to save the returned configuration as a JSON-formatted file?

A. with open(“ifaces.json”, “w”) as OutFile: OutFile.write(Response. text)
B. with open(“ifaces.json”, “w”) as OutFile: OutFile.write(Response.json())
C. with open(“ifaces.json”, “w”) as OutFile: JSONResponse = JSON.loads(Response.text) OutFile.write(JSONResponse)
D. with open(“ifaces.json”, “w”) as OutFile: OutFile.write(Response)
Correct Answer: B
The JSON() method of the Response interface takes a Response stream and reads it to completion. It returns a promise which resolves with the result of parsing the body text as JSON.
New Question 2:
Refer to the exhibit.

Which configuration must be implemented to establish EBGP peering between R1 and R2?

A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: A
New Question 3:
An engineer must configure HSRP group 300 on a Cisco IOS router. When the router is functional, it must be the active HSRP router
The peer router has been configured using the default priority value.
Which three commands are required? (Choose three.)
A. standby 300 timers 1 110
B. standby 300 priority 90
C. standby 300 priority 110
D. standby version 2
E. standby 300 preempt
F. standby version 1
Correct Answer: CDE
New Question 4:
What are the differences between TCAM and the MAC address table?
A. The MAC address table is contained in CAM ACL and QoS information is stored in TCAM
B. The MAC address table supports partial matches. TCAM requires an exact match
C. Router prefix lookups happen in CAM. MAC address table lookups happen in TCAM.
D. TCAM is used to make Layer 2 forwarding decisions CAM is used to build routing tables
Correct Answer: A
When using Ternary Content Addressable Memory (TCAM) inside routers it\’s used for faster address lookup that enables fast routing. In switches Content, Addressable Memory (CAM) is used for building and lookup of mac address table that enables L2 forwarding decisions. Besides Longest-Prefix Matching, TCAM in today\’s routers and multilayer Switch devices are used to store ACL, QoS, and other things from upper-layer processing.
New Question 5:
Which two actions, when applied in the LAN network segment, will facilitate Layer 3 CAPWAP discovery for lightweight AP? (Choose two.)
A. Utilize DHCP option 17.
B. Configure the WLC IP address on the LAN switch.
C. Utilize DHCP option 43.
D. Configure an IP helper address on the router interface
E. Enable port security on the switch port
Correct Answer: CD
In a Cisco Unified Wireless network, the LAPs must first discover and join a WLC before they can service wireless clients.
However, this presents a question: how did the LAPs find the management IP address of the controller when it is on a different subnet?
If you do not tell the LAP where the controller is via DHCP option 43, DNS resolution of “Cisco-capwapcontroller.local_domain”, or statically configure it, the LAP does not know where in the network to find the management interface of the controller.
New Question 6:
CORRECT TEXT
BGP connectivity exists between Headquarters and both remote sites; however, Remote Site 1 cannot communicate with Remote Site 2. Configure BGP according to the topology to goals:
1.
Configure R1 and R3 under the BGP process to provide reachability between Remote Site 1 and Remote Site 2. No configuration changes are permitted on R2.
2.
Ensure that the /32 networks at Remote Site 1 and Remote Site 2 can ping each other.
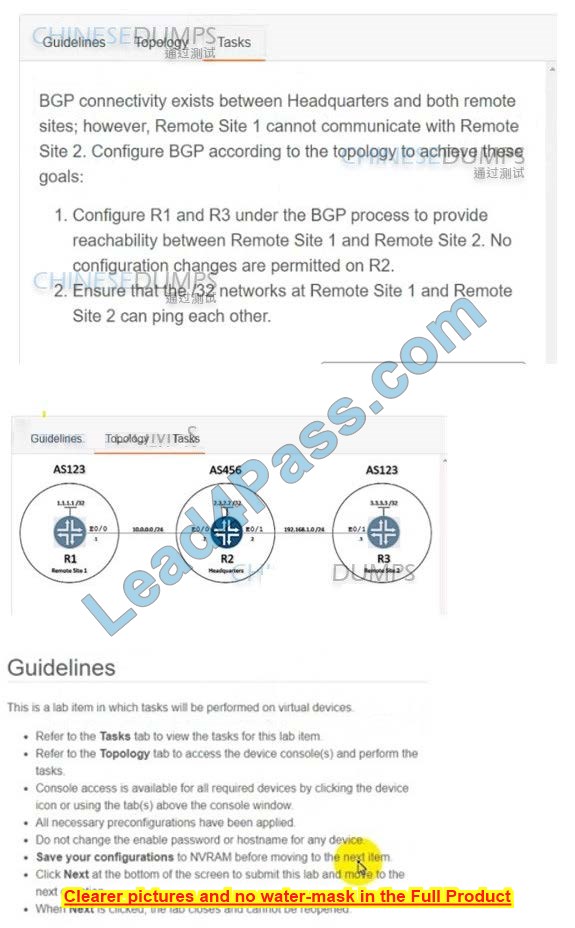
R1
R3
A. See the solution below in Explanation-
B. Place Holder
C. Place Holder
D. Place Holder
Correct Answer: A
Solution:
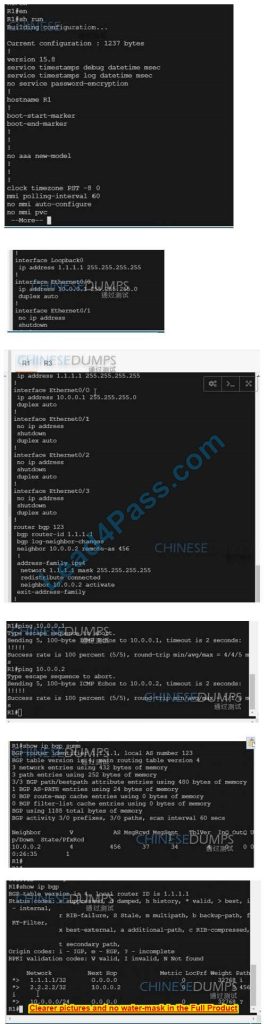
On R1:
R1(config)#router BGP 123
R1(config-router)#address-family ipv4
R1(config-router-af)#neighbor 10.0.0.2 allows-in
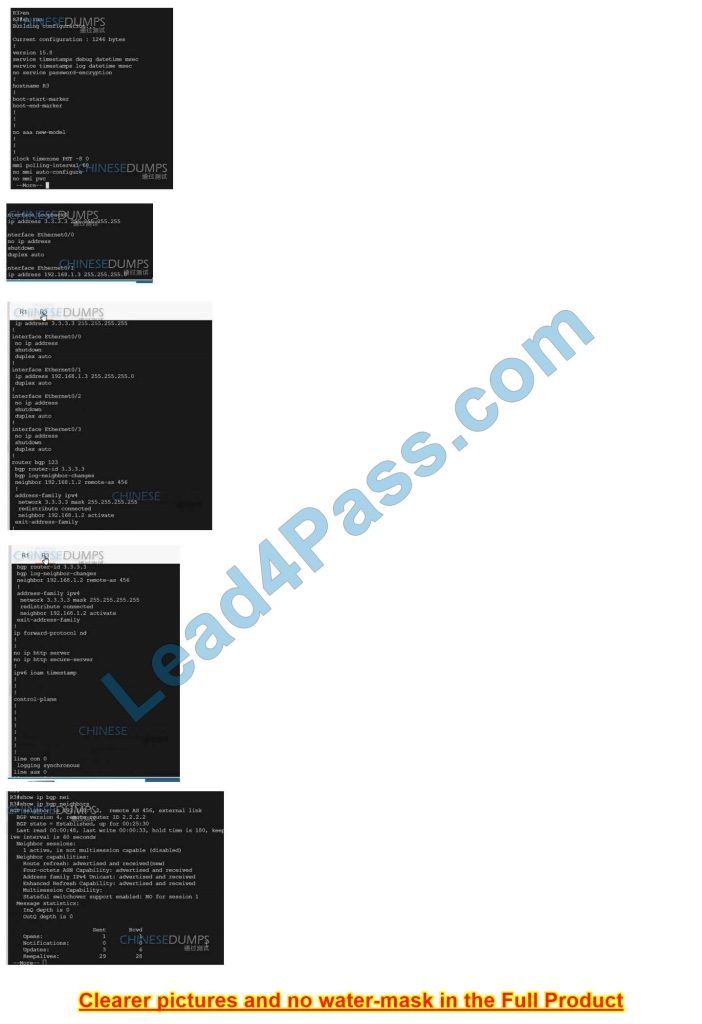
On R3:
R3(config)#router bgp 123
R3(config-router)# address-family ipv4
R3(config-router-af)#neighbor 192.168.1.2 allows-in VERIFICATION:
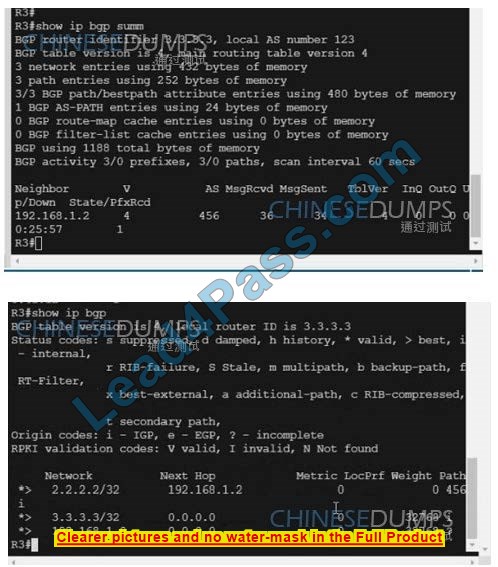
R3#sh IP route BGP
The gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnet
B 1.1.1.1 [20/0] via 192.168.1.2, 00:01:17
2.0.0.0/32 is subnetted, 1 subnet
B 2.2.2.2 [20/0] via 192.168.1.2, 00:05:06
10.0.0.0/24 is subnetted, 1 subnet
B 10.0.0.0 [20/0] via 192.168.1.2, 00:01:17
Test Ping from R3 to R1:
R3#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
!!!!!
R3#ping 1.1.1.1 source lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
A packet sent with a source address of 3.3.3.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
New Question 7:
How does CEF switching differ from process switching on Cisco devices?
A. CEF switching saves memory by sorting adjacency tables in dedicated memory on the line cards, and process switching stores all tables in the main memory
B. CEF switching uses adjacency tables built by the CDP protocol, and process switching uses the routing table
C. CEF switching uses dedicated hardware processors, and process switching uses the main processor
D. CEF switching uses a proprietary protocol based on IS-IS for MAC address lookup, and process switching uses in MAC address table
Correct Answer: B
Cisco Express Forwarding (CEF) switching is a proprietary form of scalable switching intended to tackle the problems associated with demand caching.
With CEF switching, the information which is conventionally stored in a route cache is split up over several data structures.
The CEF code is able to maintain these data structures in the Gigabit Route Processor (GRP), and also in slave processors such as the line cards in the 12000 routers.
The data structures that provide optimized lookup for efficient packet forwarding include:
1.
The Forwarding Information Base (FIB) table – CEF uses a FIB to make IP destination prefix-based switching decisions. The FIB is conceptually similar to a routing table or information base. It maintains a mirror image of the forwarding information contained in the IP routing table. When routing or topology changes occur in the network, the IP routing table is updated, and these changes are reflected in the FIB. The FIB maintains next-hop address information based on the information in the IP routing table.
2.
Because there is a one-to-one correlation between FIB entries and routing table entries, the FIB contains all known routes and eliminates the need for route cache maintenance that is associated with switching paths such as fast switching and optimum switching.
3.
Adjacency table – Nodes in the network are said to be adjacent if they can reach each other with a single hop across a link layer. In addition to the FIB, CEF uses adjacency tables to prepend Layer 2 addressing information. The adjacency table maintains Layer 2 next-hop addresses for all FIB entries.
CEF can be enabled in one of two modes:
1.
Central CEF mode – When CEF mode is enabled, the CEF FIB and adjacency tables reside on the route processor, and the route processor performs the express forwarding. You can use CEF mode when line cards are not available for CEF switching, or when you need to use features not compatible with distributed CEF switching.
2.
Distributed CEF (dCEF) mode – When dCEF is enabled, line cards maintain identical copies of the FIB and adjacency tables. The line cards can perform the express forwarding by themselves, relieving the main processor – Gigabit Route Processor (GRP) – of involvement in the switching operation. This is the only switching method available on the Cisco 12000 Series Router.
CEF uses an Inter-Process Communication (IPC) mechanism to ensure the synchronization of FIBs and adjacency tables on the route processor and line cards.
For more information about CEF switching, see Cisco Express Forwarding (CEF) White Paper.
New Question 8:
What function does vxlan perform in an SD-Access deployment?
A. policy plan forwarding
B. control plane forwarding
C. data plane forwarding
D. systems management and orchestration
Correct Answer: C
New Question 9:
An engineer must configure the strongest password authentication to locally authenticate on a router. Which configuration must be used?
A. username netadmin secret 5 $1$b1JUSkZbBS1Pyh4OzwXyZ1kSZ2
B. username netadmin secret $15b1JuSk404850110QzwXyZ1k SZ2
C. line Console 0 password $15b1Ju$
D. username netadmin secret 9 $9$vFpMfBelbRVV8SseX/bDAxtuV
Correct Answer: D
Scrypt is safer than MD5, so answer A is wrong and answer D is correct
R1(config)#username user secret 0 Specifies an UNENCRYPTED secret will follow5 Specifies an MD5 HASHED secret will follow8 Specifies a PBKDF2 HASHED secret will follow9 Specifies a SCRYPT HASHED secret will follow<0-9> Encryption types not explicitly specifiedLINE The UNENCRYPTED (cleartext) user secretLINE The UNENCRYPTED (cleartext) user secret
New Question 10:
DRAG DROP
Drag and drop the snippets onto the blanks within the code to construct a script that advertises the network prefox 192.168.5.0 session. Not all options are used.
Select and Place:
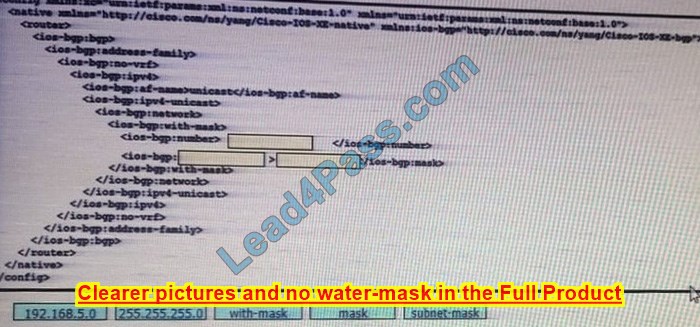
Correct Answer:
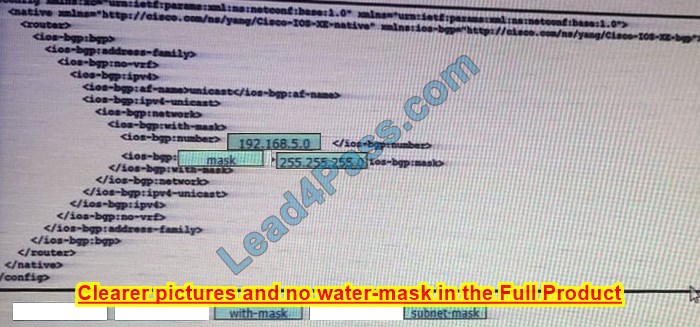
New Question 11:
A network engineer is configuring Flexible Netflow and enters these commands:
Sampler Netflow1 Mode random one-out-of 100 Interface fastethernet 1/0 Flow-sampler netflow1
Which are two results of implementing this feature instead of traditional Netflow? (Choose two.)
A. CPU and memory utilization are reduced.
B. Only the flows of top 100 talkers are exported
C. The data export flow is more secure.
D. The number of packets to be analyzed are reduced
E. The accuracy of the data to be analyzed is improved
Correct Answer: AD
New Question 12:
Which benefit is offered by a cloud infrastructure deployment but is lacking in an on-premises deployment?
A. efficient scalability
B. virtualization
C. storage capacity
D. supported systems
Correct Answer: A
New Question 13:
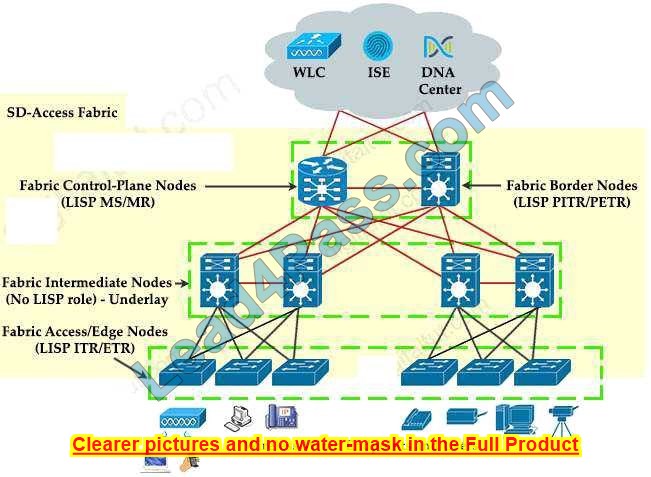
What are two device roles in Cisco SD-Access fabric? (Choose two.)
A. core switch
B. vBond controller
C. edge node
D. access switch
E. border node
Correct Answer: CE
There are five basic device roles in the fabric overlay:
+
Control plane node: This node contains the settings, protocols, and mapping tables to provide the endpoint-to-location (EID-to-RLOC) mapping system for the fabric overlay. + Fabric border node: This fabric device (for example, core layer device) connects external Layer 3 networks to the SDA fabric.
+
Fabric edge node: This fabric device (for example, access or distribution layer device) connects wired endpoints to the SDA fabric.
+
Fabric WLAN controller (WLC): This fabric device connects APs and wireless endpoints to the SDA fabric.
+
Intermediate nodes: These are intermediate routers or extended switches that do not provide any sort of SD-Access fabric role other than underlay services.
New Question 14:
What is a fact about Cisco EAP-FAST?
A. It does not require a RADIUS server certificate.
B. It requires a client certificate.
C. It is an IETF standard.
D. It operates in transparent mode.
Correct Answer: A

New Question 15:
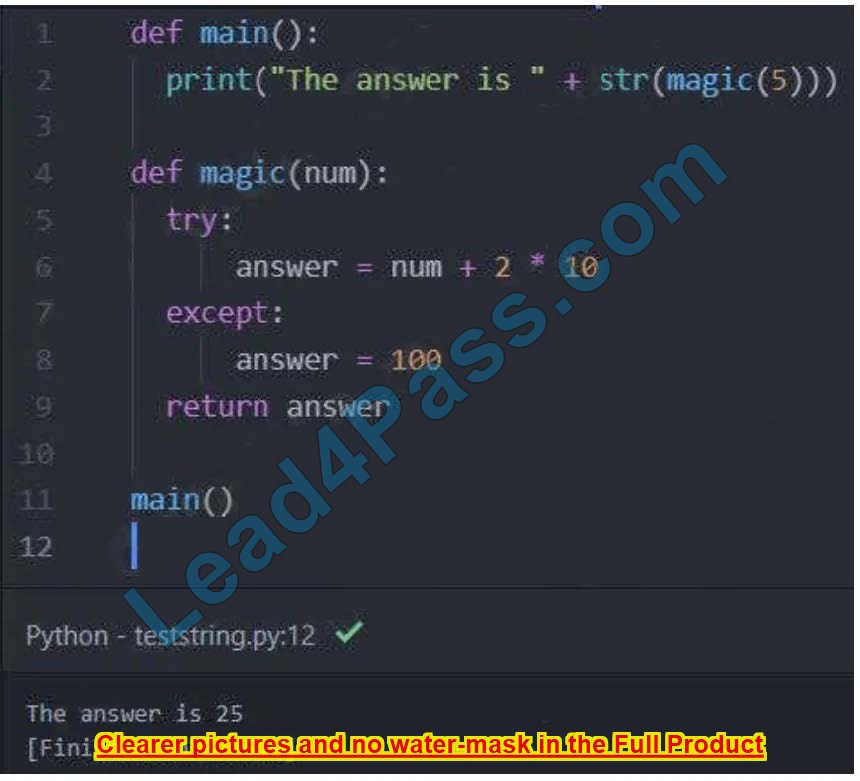
Refer to the exhibit. What is displayed when the code is run?

A. The answer is 25
B. The answer is 70
C. The answer is 5
D. The answer is 100
Correct Answer: A
The “magic” function receives a number, which is 5 from the main() in this question. This function returns a result of 5 + 2*10 = 25 and the str() function converts it into a string (“25”) before printing to the terminal.
…
The leads4pass 350-401 dumps are really effective in Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) exam prep material.
Use the New 350-401 dumps https://www.leads4pass.com/350-401.html to ensure you pass the Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) exam with ease.
BTW, giving away some free Cisco 350-401 pdfs for candidate reference:
https://drive.google.com/file/d/1fYt1qLwW_w51z4Gr4pUOqVnyab6Ioeg3/view?usp=share_link
https://drive.google.com/file/d/1UZ1OCWXuClKs73-SDQXFO8j-oA4A8a8Q/view?usp=share_link
https://drive.google.com/file/d/1CzUD7IShCoh1JNUYek2Q2REVIzJprjMs/view?usp=share_link
https://drive.google.com/file/d/1ahrnRyvF4ubbTamp6ejufmuvDDV3xA_H/view?usp=share_link
https://drive.google.com/file/d/14FtbIb6_G2tGECN_fvyVIxB7I8VqpH8r/view?usp=share_link


