To earn Cisco Certified CyberOps Professional certification | Exam Materials
To earn the Cisco Certified CyberOps Professional certification, you must pass two exams, Core exam 350-201 CBRCOR and Concentration exam 300-215 CBRFIR:
Each of these exams will lead to a separate Specialist certification, although both exams must be passed to earn the Cisco Certified CyberOps Professional certification.
How do I earn the Cisco Certified CyberOps Professional certification?
Use the exam materials to help you successfully pass the Cisco Certified CyberOps Professional certification exam:
350-201 CBRCOR exam dumps material download: https://www.leads4pass.com/350-201.html
300-215 CBRFIR exam dumps material download: https://www.leads4pass.com/300-215.html
The real exam dumps include both PDF and VCE study tools, which you can see in the leads4pass exam dumps page, to help you achieve easy exam success.
Cisco Certified CyberOps Professional certification exam details:
Concentration exam 300-215 CBRFIR:
Vendor: Cisco
Exam Code: 300-215
Exam Name: Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps (CBRFIR)
Certification: Cisco Certified CyberOps Specialist – CyberOps Forensic Analysis and Incident Response
Duration: 90 minutes
Languages: English
Price: $300 USD
Core exam 350-201 CBRCOR:
Vendor: Cisco
Exam Code: 350-201
Exam Name: Performing CyberOps Using Cisco Security Technologies (CBRCOR)
Certification: Cisco Certified CyberOps Specialist – CyberOps Core
Duration: 120 minutes
Languages: English
Price: $400 USD
Free to share some 350-201 CBRCOR online exam practice:
QUESTION 1:
Refer to the exhibit. Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE detects the threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a quarantine VLAN using Adaptive Network Control policy.
Which method was used to signal ISE to quarantine the endpoints?
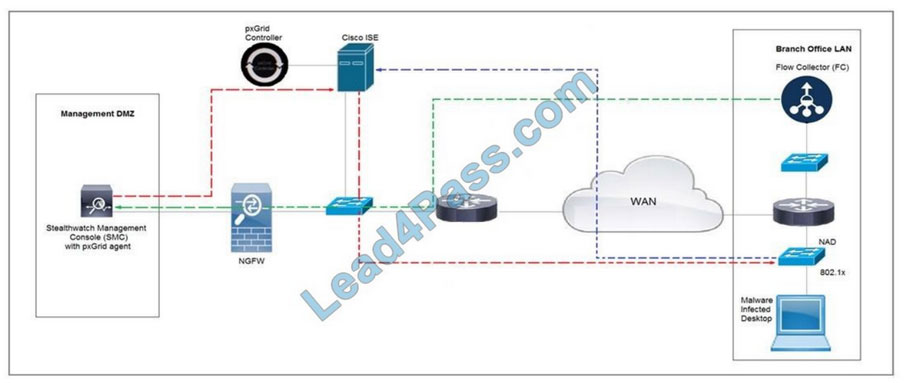
A. SNMP
B. syslog
C. REST API
D. pxGrid
Correct Answer: C
QUESTION 2:
An engineer is developing an application that requires frequent updates to close feedback loops and enable teams to quickly apply patches. The team wants their code updates to get to market as often as possible.
Which software development approach should be used to accomplish these goals?
A. continuous delivery
B. continuous integration
C. continuous deployment
D. continuous monitoring
Correct Answer: A
QUESTION 3:
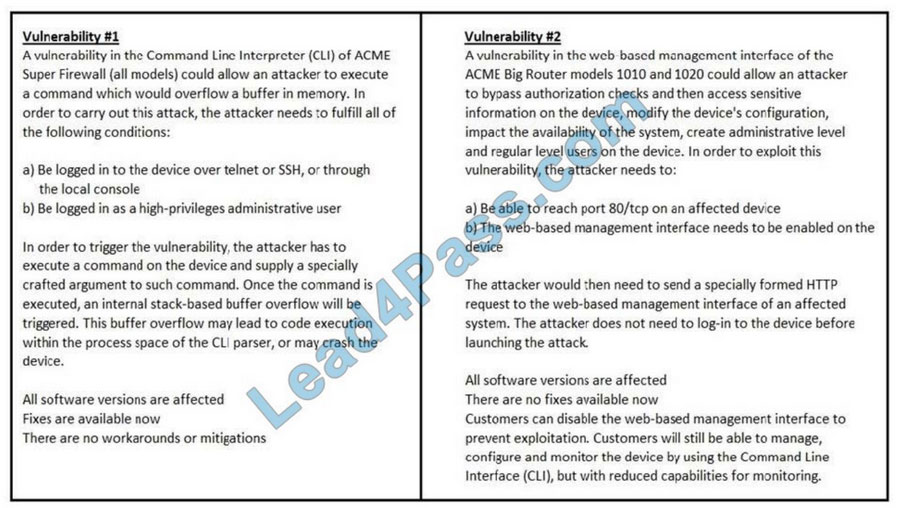
Refer to the exhibit. How must these advisories be prioritized for handling?
A. The highest priority for handling depends on the type of institution deploying the devices
B. Vulnerability #2 is the highest priority for every type of institution
C. Vulnerability #1 and vulnerability #2 have the same priority
D. Vulnerability #1 is the highest priority for every type of institution
Correct Answer: D
QUESTION 4:
Refer to the exhibit. Where is the MIME type that should be followed indicated?
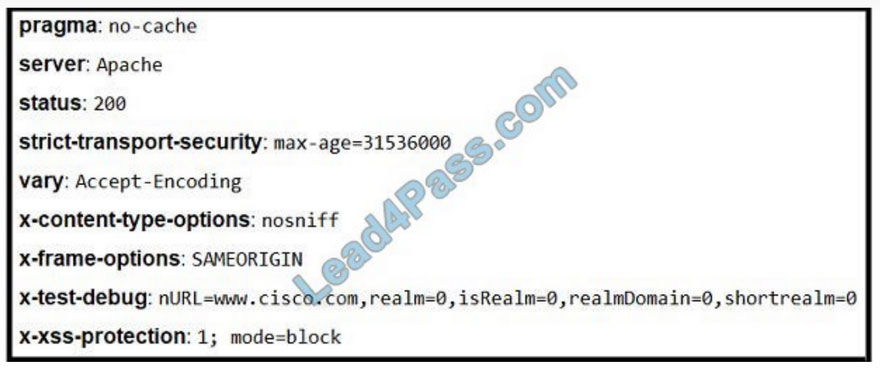
A. x-test-debug
B. strict-transport-security
C. x-xss-protection
D. x-content-type-options
Correct Answer: A
QUESTION 5:
A security architect is working in a processing center and must implement a DLP solution to detect and prevent any type of copy and paste attempts of sensitive data within unapproved applications and removable devices.
Which technical architecture must be used?
A. DLP for data in motion
B. DLP for removable data
C. DLP for data in use
D. DLP for data at rest
Correct Answer: C
Reference: https://www.endpointprotector.com/blog/what-is-data-loss-prevention-dlp/
QUESTION 6:
DRAG DROP
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during the phases on the right.
Select and Place:
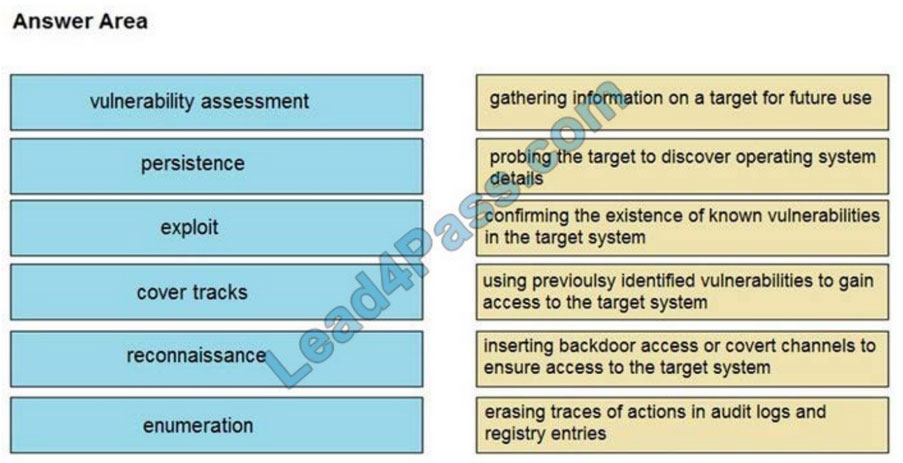
Correct Answer:
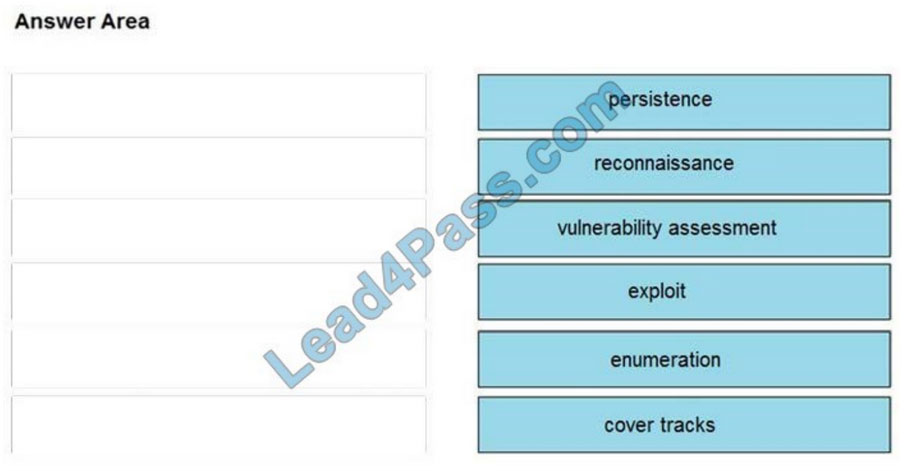
QUESTION 7:
DRAG DROP
An organization lost connectivity to critical servers, and users cannot access business applications and internal websites. An engineer checks the network devices to investigate the outage and determines that all devices are functioning. Drag and drop the steps from the left into the sequence on the right to continue investigating this issue. Not all options are used.
Select and Place:
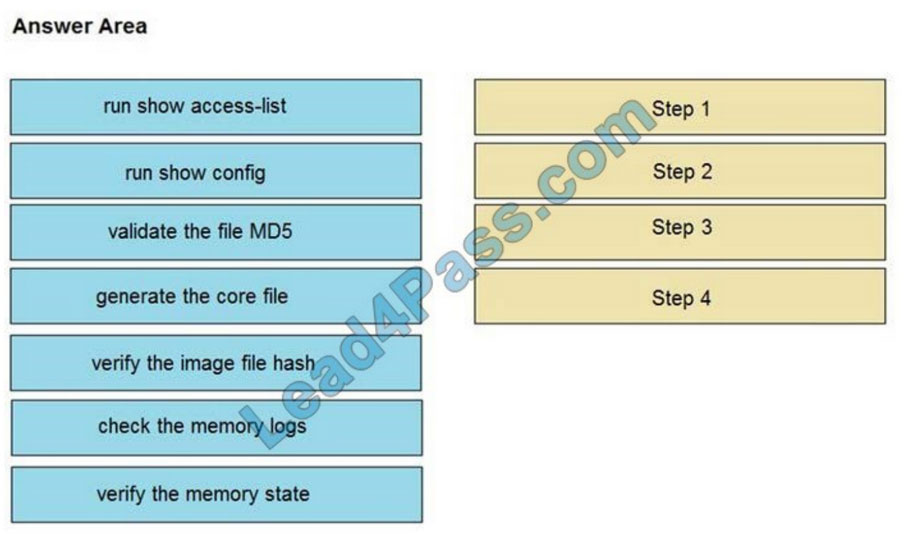
Correct Answer:
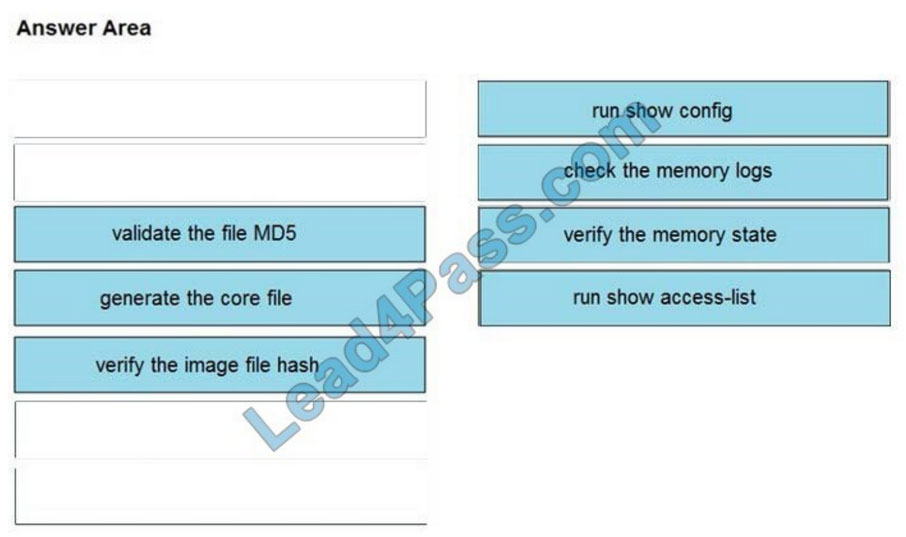
QUESTION 8:
What is a principle of Infrastructure as Code?
A. System maintenance is delegated to software systems
B. Comprehensive initial designs support robust systems
C. Scripts and manual configurations work together to ensure repeatable routines
D. System downtime is grouped and scheduled across the infrastructure
Correct Answer: B
QUESTION 9:
An employee abused PowerShell commands and script interpreters, which lead to an indicator of compromise (IOC) trigger. The IOC event shows that a known malicious file has been executed, and there is an increased likelihood of a breach.
Which indicator generated this IOC event?
A. ExecutedMalware.ioc
B. Crossrider.ioc
C. ConnectToSuspiciousDomain.ioc
D. W32 AccesschkUtility.ioc
Correct Answer: D
QUESTION 10:
Refer to the exhibit. Which indicator of compromise is represented by this STIX?

A. website redirecting traffic to ransomware server
B. website hosting malware to download files
C. web server vulnerability exploited by malware
D. cross-site scripting vulnerability to backdoor server
Correct Answer: C
QUESTION 11:
A security expert is investigating a breach that resulted in a $32 million loss from customer accounts. Hackers were able to steal API keys and two-factor codes due to a vulnerability that was introduced in a new code a few weeks before the attack.
Which step was missed that would have prevented this breach?
A. use of the Nmap tool to identify the vulnerability when the new code was deployed
B. implementation of a firewall and intrusion detection system
C. implementation of an endpoint protection system
D. use of SecDevOps to detect the vulnerability during development
Correct Answer: D
Reference: https://securityintelligence.com/how-to-prioritize-security-vulnerabilities-in-secdevops/
QUESTION 12:
Which command does an engineer use to set read/write/execute access on a folder for everyone who reaches the resource?
A. chmod 666
B. chmod 774
C. chmod 775
D. chmod 777
Correct Answer: D
Reference: https://www.pluralsight.com/blog/it-ops/linux-file-permissions
QUESTION 13:
An analyst is alerted for a malicious file hash. After analysis, the analyst determined that an internal workstation is communicating over port 80 with an external server and that the file hash is associated with Duqu malware.
Which tactics, techniques, and procedures align with this analysis?
A. Command and Control, Application Layer Protocol, Duqu
B. Discovery, Remote Services: SMB/Windows Admin Shares, Duqu
C. Lateral Movement, Remote Services: SMB/Windows Admin Shares, Duqu
D. Discovery, System Network Configuration Discovery, Duqu
Correct Answer: A
……
[PDF Download] 350-201 CBRCOR Online Exam Practice Free Download: https://drive.google.com/file/d/1AWESvo5Beac9z16xeX9pw-cyNhDM0Cnc/
Tip: 300-215 CBRFIR online exam practice will not be shared temporarily, you can download the free demo in leads4pass
Click here for the complete set of Cisco Certified CyberOps Professional certification exam materials.
