We share the latest exam dumps throughout the year to help you improve your skills and experience! The latest Cisco CCNA Cyber Ops 210-255 exam
dumps, online exam Practice test to test your strength, Cisco 210-255 “Implementing Cisco Cybersecurity Operations (SECOPS) v1.0” in https://www.leads4pass.com/210-255.html Update the exam content throughout the year to ensure that all exam content is authentic and valid. 210-255 PDF Online download for easy learning.
[PDF] Free Cisco CCNA Cyber Ops 210-255 pdf dumps download from Google Drive: https://drive.google.com/open?id=1DvJqIWfL52ROsKHiVgNW44JumpzOCCj_
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
210-255 SECOPS – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/secops.html
Free test Cisco CCNA Cyber Ops 210-255 Exam questions and Answers
QUESTION 1
What is the common artifact that is used to uniquely identify a detected file?
A. Hash
B. Timestamp
C. File size
Correct Answer: A
QUESTION 2
Which CVSSv3 Attack Vector metric value requires the attacker to physically touch or manipulate the vulnerable
component?
A. local
B. physical
C. network
D. adjacent
Correct Answer: B
QUESTION 3
Which element is included in an incident response plan?
A. organization mission
B. junior analyst approval
C. day-to-day firefighting
D. siloed approach to communications
Correct Answer: A
QUESTION 4
Which of the following is an example of a managed security offering where incident response experts monitor and
respond to security alerts in a security operations center (SOC)?
A. Cisco CloudLock
B. Cisco\\’s Active Threat Analytics (ATA)
C. Cisco Managed Firepower Service
D. Cisco Jasper
Correct Answer: B
QUESTION 5
Which option is unnecessary for determining the appropriate containment strategy according to NIST.SP800-61 r2?
A. effectiveness of the strategy
B. time and resource needed to implement the strategy
C. need for evidence preservation
D. attack vector used to compromise the system
Correct Answer: D
QUESTION 6
Which CVSSv3 metric value increases when the attacker is able to modify all files protected by the vulnerable
component?
A. confidentiality
B. integrity
C. availability
D. complexity
Correct Answer: B
QUESTION 7
Which of the following is true about attribution in a cybersecurity investigation?
A. A suspect-led approach is often accepted in supreme courts.
B. A suspect-led approach is pejorative and often biased to the disadvantage of those being investigated.
C. A suspect-led approach is mostly used in corporate investigations.
D. A suspect-led approach is mostly used in private investigations.
Correct Answer: B
QUESTION 8
Which component of the NIST SP800-61 r2 incident handling strategy reviews data?
A. preparation
B. detection and analysis
C. containment, eradication, and recovery
D. post-incident analysis
Correct Answer: D
QUESTION 9
Refer to the Exhibit. A customer reports that they cannot access your organization\\’s website. Which option is a
possible reason that the customer cannot access the website?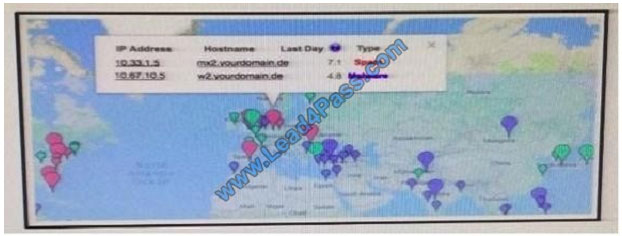
A. The server at 10.33.1.5 is using up too much bandwidth causing a denial- of-service.
B. The server at 10.67.10.5 has a virus.
C. A vulnerability scanner has shown that 10.67.10.5 has been compromised.
D. Web traffic sent from 10.67.10.5 has been identified as malicious by Internet sensors.
Correct Answer: D
QUESTION 10
Which analyzing technique describe the outcome as well as how likely each outcome is?
A. deterministic
B. exploratory
C. probabilistic
D. descriptive
Correct Answer: C
QUESTION 11
Which network device creates and sends the initial packet of a session?
A. source
B. origination
C. destination
D. network
Correct Answer: A
QUESTION 12
At which stage attacking the vulnerability belongs in Cyber kill chain?
A. Exploitation
B. Reconnaissance
C. Weaponization
D. Delivery
E. Installation
F. Command and control (C2)
G. Actions on objectives
Correct Answer: A
QUESTION 13
Which element can be used by a threat actor to discover a possible opening into a target network and can also be used
by an analyst to determine the protocol of the malicious traffic?
A. TTLs
B. ports
C. SMTP replies
D. IP addresses
Correct Answer: B
We share 13 of the latest Cisco CCNA Cyber Ops 210-255 exam dumps and 210-255 pdf online download for free. Now you know what you’re capable of! If you’re just interested in this, please keep an eye on “Dumpinside.com” blog updates! If you want to get the Cisco CCNA Cyber Ops 210-255 Exam Certificate: https://www.leads4pass.com/210-255.html (Total questions:170 Q&A).
Related 210-255 Popular Exam resources
| title | youtube | 210-255 SECOPS – Cisco | leads4pass | |
|---|---|---|---|---|
| Cisco 210-255 | leads4pass 210-255 dumps pdf | leads4pass 210-255 youtube | 210-255 SECOPS – Cisco | https://www.leads4pass.com/210-255.html |
| Cisco CCNA Cyber Ops | https://www.leads4pass.com/210-255.html | |||
| https://www.leads4pass.com/210-250.html |
leads4pass Promo Code 12% Off

Why Choose leads4pass?
leads4pass helps you pass the exam easily! We compare data from all websites in the network, other sites are expensive,
and the data is not up to date, leads4pass updates data throughout the year. The pass rate of the exam is above 98.9%.




