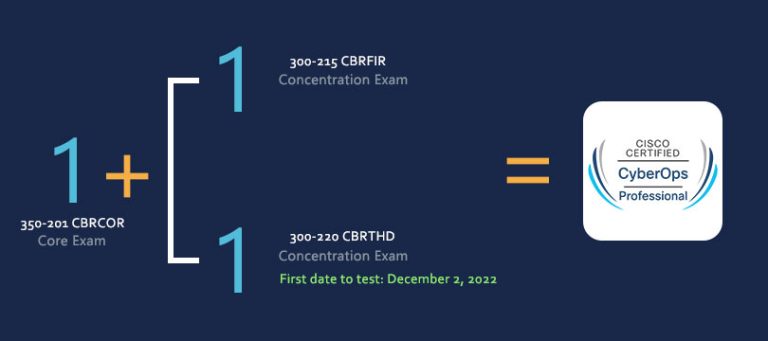
[Update Nov 2022] CyberOps Professional 300-215 dumps with PDF and VCE
New updated CyberOps Professional 300-215 dumps with the PDF download file and VCE mock exam engine, 59 newly updated exam questions, and answers, verified by CyberOps Professional experts to ensure validity. Download CyberOps Professional 300-215 dumps: https://www.leads4pass.com/300-215.html Practice the complete exam questions to help you easily pass the 300-215 CBRFIR certification exam. Candidates for the […]
9 mins read