Latest CompTIA Security+ SY0-401 dumps exam training resources in PDF format download free try from lead4pass. “CompTIA Security+ Certification” is the name of CompTIA Security+ https://www.leads4pass.com/sy0-401.html exam dumps which covers all the knowledge points of the real CompTIA exam. High quality CompTIA Security+ SY0-401 dumps vce youtube demo update free shared. 100% success and guarantee to pass CompTIA SY0-401 exam.
Get your CompTIA Security+ SY0-401 dumps exam preparation questions in form of SY0-401 PDF. If you want to get success with good grades then these CompTIA Security+ SY0-401 dumps exam question and answers are splendid platform for you I personally review this web many times that’s why I am suggesting you this one.
Vendor: CompTIA
Certifications: Security+
Exam Name: CompTIA Security+ Certification
Exam Code: SY0-401
Total Questions: 1776 Q&As
Download latest CompTIA SY0-401 dumps pdf training resources: https://drive.google.com/open?id=0B_7qiYkH83VRMEhpY1lTQnR4NDA
Download latest CompTIA SY0-101 dumps pdf training resources: https://drive.google.com/open?id=0B_7qiYkH83VRWm1VeWl0ZVhINkk
Best CompTIA Security+ SY0-401 Dumps Exam Questions And Answers (Q1-Q40)
QUESTION 1
Ann is the data owner of financial records for a company. She has requested that she have the ability to assign read and write privileges to her folders. The network administrator is tasked with setting up the initial access control system and handing Ann’s administrative capabilities. Which of the following systems should be deployed?
A. Role-based
B. Mandatory
C. Discretionary
D. Rule-based
Correct Answer: C
QUESTION 2
A password history value of three means which of the following?
A. Three different passwords are used before one can be reused.
B. A password cannot be reused once changed for three years.
C. After three hours a password must be re-entered to continue.
D. The server stores passwords in the database for three days.
Correct Answer: A
QUESTION 3
A security administrator has installed a new KDC for the corporate environment. Which of the following authentication protocols is the security administrator planning to implement across the organization?
A. LDAP
B. RADIUS
C. Kerberos
D. XTACACS
Correct Answer: C
QUESTION 4
A system administrator is using a packet sniffer to troubleshoot remote authentication. The administrator detects a device trying to communicate to TCP port 49. Which of the following authentication methods is MOST likely being attempted?
A. RADIUS
B. TACACS+
C. Kerberos
D. LDAP
Correct Answer: B
QUESTION 5
Which of the following authentication services requires the use of a ticket-granting ticket (TGT) server in order to complete the authentication process?
A. TACACS+
B. Secure LDAP
C. RADIUS
D. Kerberos
Correct Answer: D
QUESTION 6
An organization has introduced token-based authentication to system administrators due to risk of password compromise. The tokens have a set of numbers that automatically change every 30 seconds. Which of the following type of authentication mechanism is this?
A. TOTP
B. Smart card
C. CHAP
D. HOTP
Correct Answer: A
QUESTION 7
The security department has implemented a new laptop encryption product in the environment. The product requires one user name and password at the time of boot up and also another password after the operating system has finished loading. This setup is using which of the following authentication types?
A. Two-factor authentication
B. Single sign-on
C. Multifactor authentication
D. Single factor authentication
Correct Answer: D
QUESTION 8
A company hired Joe, an accountant. The IT administrator will need to create a new account for Joe. The company uses groups for ease of management and administration of user accounts. SY0-401 dumps
Joe will need network access to all directories, folders and files within the accounting department.
Which of the following configurations will meet the requirements?
A. Create a user account and assign the user account to the accounting group.
B. Create an account with role-based access control for accounting.
C. Create a user account with password reset and notify Joe of the account creation.
D. Create two accounts: a user account and an account with full network administration rights.
Correct Answer: B
QUESTION 9
Which of the following access controls enforces permissions based on data labeling at specific levels?
A. Mandatory access control
B. Separation of duties access control
C. Discretionary access control
D. Role based access control
Correct Answer: A
QUESTION 10
A system administrator needs to ensure that certain departments have more restrictive controls to their shared folders than other departments. Which of the following security controls would be implemented to restrict those departments?
A. User assigned privileges
B. Password disablement
C. Multiple account creation
D. Group based privileges
Correct Answer: D
QUESTION 11
Ann was reviewing her company’s event logs and observed several instances of GUEST accessing the company print server, file server, and archive database. As she continued to investigate, Ann noticed that it seemed to happen at random intervals throughout the day, but mostly after the weekly automated patching and often logging in at the same time. Which of the following would BEST mitigate this issue?
A. Enabling time of day restrictions
B. Disabling unnecessary services
C. Disabling unnecessary accounts
D. Rogue machine detection
Correct Answer: C
QUESTION 12
An administrator implements SELinux on a production web server. After implementing this, the web server no longer serves up files from users’ home directories. To rectify this, the administrator creates a new policy as the root user. This is an example of which of the following? (Select TWO).
A. Enforcing SELinux in the OS kernel is role-based access control
B. Enforcing SELinux in the OS kernel is rule-based access control
C. The policy added by the root user is mandatory access control
D. Enforcing SELinux in the OS kernel is mandatory access control
E. The policy added by the root user is role-based access control
F. The policy added by the root user is rule-based access control
Correct Answer: DF
QUESTION 13
Jane, a security administrator, has been tasked with explaining authentication services to the company’s management team. The company runs an active directory infrastructure. Which of the following solutions BEST relates to the host authentication protocol within the company’s environment?
A. Kerberos
B. Least privilege
C. TACACS+
D. LDAP
Correct Answer: A
QUESTION 14
Which of the following is an example of multifactor authentication?
A. Credit card and PIN
B. Username and password
C. Password and PIN
D. Fingerprint and retina scan
Correct Answer: A
QUESTION 15
Which of the following should be used to authenticate and log connections from wireless users connecting with EAP-TLS?
A. Kerberos
B. LDAP
C. SAML
D. RADIUS
Correct Answer: D
QUESTION 16
Which of the following authentication services uses a ticket granting system to provide access?
A. RADIUS
B. LDAP
C. TACACS+
D. Kerberos
Correct Answer: D
QUESTION 17
Which of the following was based on a previous X.500 specification and allows either unencrypted authentication or encrypted authentication through the use of TLS?
A. Kerberos
B. TACACS+
C. RADIUS
D. LDAP
Correct Answer: D
QUESTION 18
Which of the following types of security services are used to support authentication for remote users and devices?
A. Biometrics
B. HSM
C. RADIUS
D. TACACS
Correct Answer: C
QUESTION 19
A hacker has discovered a simple way to disrupt business for the day in a small company which relies on staff working remotely. In a matter of minutes the hacker was able to deny remotely working staff access to company systems with a script. Which of the following security controls is the hacker exploiting?
A. DoS
B. Account lockout
C. Password recovery
D. Password complexity
Correct Answer: B
QUESTION 20
A technician is reviewing the logical access control method an organization uses. One of the senior managers requests that the technician prevent staff members from logging on during nonworking days. Which of the following should the technician implement to meet managements request?
A. Enforce Kerberos
B. Deploy smart cards
C. Time of day restrictions
D. Access control lists
Correct Answer: C
QUESTION 21
Which of the following is the BEST reason for placing a password lock on a mobile device?
A. Prevents an unauthorized user from accessing owner’s data
B. Enables remote wipe capabilities
C. Stops an unauthorized user from using the device again
D. Prevents an unauthorized user from making phone calls
Correct Answer: A
QUESTION 22
Which of the following is mainly used for remote access into the network?
A. XTACACS
B. TACACS+
C. Kerberos
D. RADIUS
Correct Answer: D
QUESTION 23
Which of the following protocols uses TCP instead of UDP and is incompatible with all previous versions?
A. TACACS
B. XTACACS
C. RADIUS
D. TACACS+
Correct Answer: D
QUESTION 24
The system administrator is tasked with changing the administrator password across all 2000 computers in the organization. SY0-401 dumps Which of the following should the system administrator implement to accomplish this task?
A. A security group
B. A group policy
C. Key escrow
D. Certificate revocation
Correct Answer: B
QUESTION 25
The IT department has setup a website with a series of questions to allow end users to reset their own accounts. Which of the following account management practices does this help?
A. Account Disablements
B. Password Expiration
C. Password Complexity
D. Password Recovery
Correct Answer: D
QUESTION 26
Use of group accounts should be minimized to ensure which of the following?
A. Password security
B. Regular auditing
C. Baseline management
D. Individual accountability
Correct Answer: D
QUESTION 27
One of the most basic ways to protect the confidentiality of data on a laptop in the event the device is physically stolen is to implement which of the following?
A. File level encryption with alphanumeric passwords
B. Biometric authentication and cloud storage
C. Whole disk encryption with two-factor authentication
D. BIOS passwords and two-factor authentication
Correct Answer: C
QUESTION 28
A security analyst implemented group-based privileges within the company active directory. Which of the following account management techniques should be undertaken regularly to ensure least privilege principles?
A. Leverage role-based access controls.
B. Perform user group clean-up.
C. Verify smart card access controls.
D. Verify SHA-256 for password hashes.
Correct Answer: B
QUESTION 29
An internal auditing team would like to strengthen the password policy to support special characters. Which of the following types of password controls would achieve this goal?
A. Add reverse encryption
B. Password complexity
C. Increase password length
D. Allow single sign on
Correct Answer: B
QUESTION 30
Which of the following is best practice to put at the end of an ACL?
A. Implicit deny
B. Time of day restrictions
C. Implicit allow
D. SNMP string
Correct Answer: A
QUESTION 31
Ann, a security administrator, wishes to replace their RADIUS authentication with a more secure protocol, which can utilize EAP. Which of the following would BEST fit her objective?
A. CHAP
B. SAML
C. Kerberos
D. Diameter
Correct Answer: D
QUESTION 32
Jane, a security administrator, needs to implement a secure wireless authentication method that uses a remote RADIUS server for authentication.
Which of the following is an authentication method Jane should use?
A. WPA2-PSK
B. WEP-PSK
C. CCMP
D. LEAP
Correct Answer: D
QUESTION 33
A network administrator is configuring access control for the sales department which has high employee turnover. Which of the following is BEST suited when assigning user rights to individuals in the sales department?
A. Time of day restrictions
B. Group based privileges
C. User assigned privileges
D. Domain admin restrictions
Correct Answer: B
QUESTION 34
A security technician is working with the network firewall team to implement access controls at the company’s demarc as part of the initiation of configuration management processes. One of the network technicians asks the security technician to explain the access control type found in a firewall. With which of the following should the security technician respond?
A. Rule based access control
B. Role based access control
C. Discretionary access control
D. Mandatory access control
Correct Answer: A
QUESTION 35
A security administrator has been tasked to ensure access to all network equipment is controlled by a central server such as TACACS+. This type of implementation supports which of the following risk mitigation strategies?
A. User rights and permissions review
B. Change management
C. Data loss prevention
D. Implement procedures to prevent data theft
Correct Answer: A
QUESTION 36
Which of the following is an XML based open standard used in the exchange of authentication and authorization information between different parties?
A. LDAP
B. SAML
C. TACACS+
D. Kerberos
Correct Answer: B
QUESTION 37
The security manager wants to unify the storage of credential, phone numbers, office numbers, and address information into one system. Which of the following is a system that will support the requirement on its own?
A. LDAP
B. SAML
C. TACACS
D. RADIUS
Correct Answer: A
QUESTION 38
LDAP and Kerberos are commonly used for which of the following?
A. To perform queries on a directory service
B. To store usernames and passwords for Federated Identity
C. To sign SSL wildcard certificates for subdomains
D. To utilize single sign-on capabilities
Correct Answer: D
QUESTION 39
A user reports being unable to access a file on a network share. SY0-401 dumps The security administrator determines that the file is marked as confidential and that the user does not have the appropriate access level for that file. Which of the following is being implemented?
A. Mandatory access control
B. Discretionary access control
C. Rule based access control
D. Role based access control
Correct Answer: A
QUESTION 40
Users report that they are unable to access network printing services. The security technician checks the router access list and sees that web, email, and secure shell are allowed. Which of the following is blocking network printing?
A. Port security
B. Flood guards
C. Loop protection
D. Implicit deny
Correct Answer: D
Useful CompTIA Security+ SY0-401 dumps pdf practice files and study guides free download from lead4pass. The best and most updated latest CompTIA Security+ https://www.leads4pass.com/sy0-401.html dumps pdf training resources which are the best for clearing SY0-401 exam test, and to get certified by CompTIA Security+. If you are looking to get CompTIA Security+ Certification by passing exam SY0-401 then you can pass it in one go.
High quality CompTIA Security+ SY0-401 dumps vce youtube demo:
https://youtu.be/Ti0gVvsg5eI
The Following Are Some Reviews From Our Customers:
You can click here to have a review about us: https://www.resellerratings.com/store/lead4pass
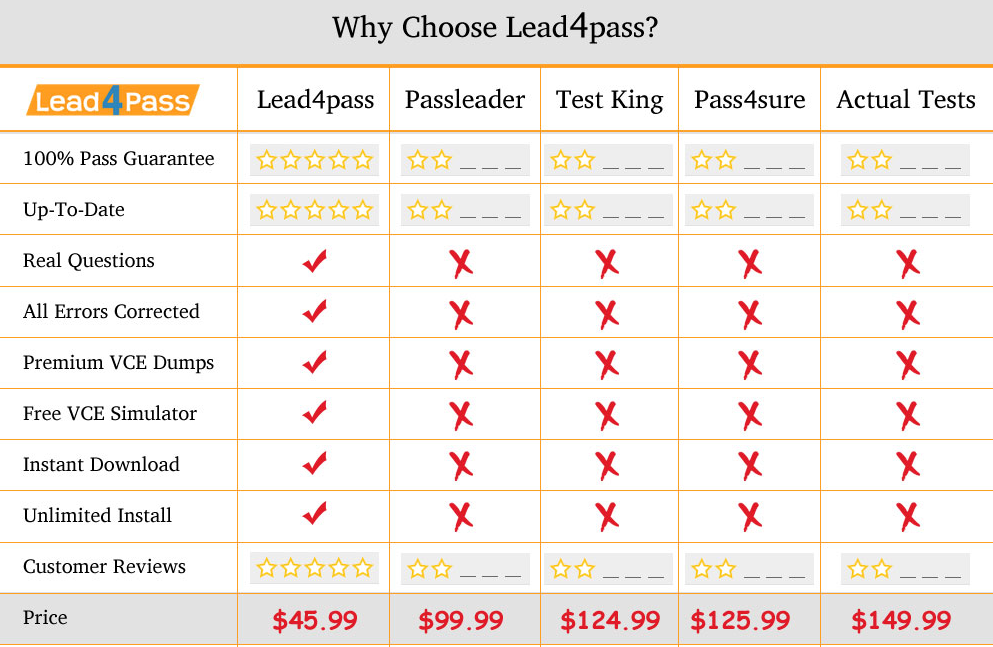
Why Select Lead4pass?
Lead4pass is the best provider of IT learning materials and the right choice for you to prepare for CompTIA Security+ SY0-401 exam. Other brands started earlier, but the price is relatively expensive and the questions are not the newest. Lead4pass provide the latest real questions and answers with lowest prices, help you pass CompTIA SY0-401 exam easily at first try.